VBScrambler is a Python based VBScript code obfuscator which essentially takes VBScript as a form of input, either file or inline code, and provides an obfuscated VBScript one liner as output. The obfuscation works by taking the original VBScript, performing a byte shift on the supplied code. It will then take the garbage-looking code and insert it into a randomly generated deobfuscation script in VB, which will reverse the byte shift and then execute its contents.
The shift works similar to ROT13 with a randomly supplied shift value ranging from -5 to 7. Larger numbers tend to prevent the generated script from executing, producing errors. Other errors can occur when copying generated code from console, as special characters, especially in Linux, may not copy correctly.
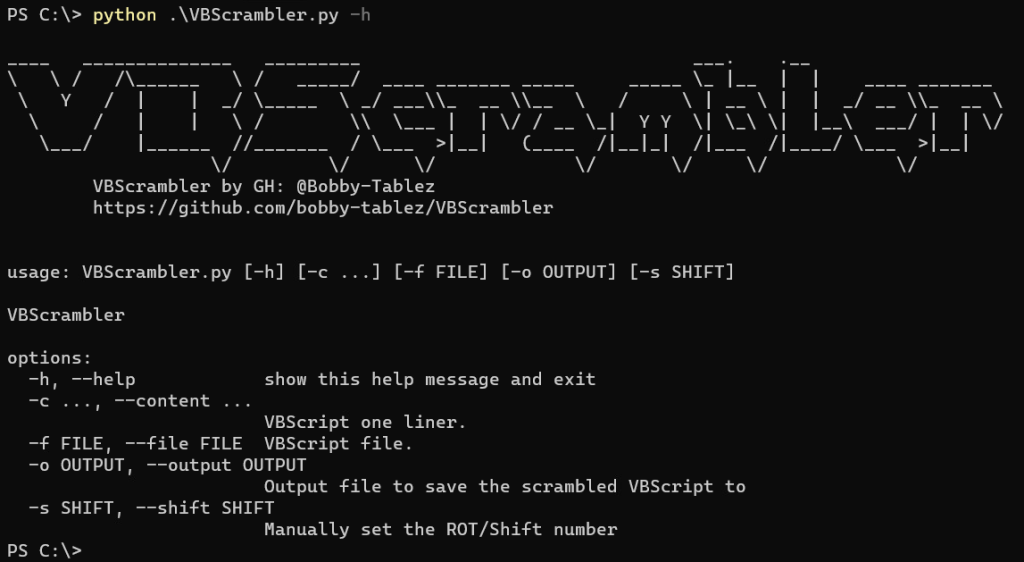
-c, --contentSupply inline VBScript. (This must be the last argument supplied)-f, --fileSupply a .vbs file to obfuscate (supports multi-line)-o, --outputSave generated output to file [filename.vbs]-s, --shiftManually specify a shift value If no argument is provided, the script will prompt the user for code to obfuscate.
Installation:
Requires Python v3.8+ Either download and execute VBScrambler.py file manually on Windows or Linux, or install and run via pypi package:
pip install VBScrambler
PyPi Package:
https://pypi.org/project/VBScrambler/
Example:
Obfuscating the following VBScript using the command:
python3 VBScrambler.py -s 5 -f ps.vbs
Dim shell,command
command = "powershell.exe -nologo -command ""New-Item C:\text\vbstest.txt -Force"""
Set shell = CreateObject("WScript.Shell")
shell.Run command,0
Generates the following VBScript code:
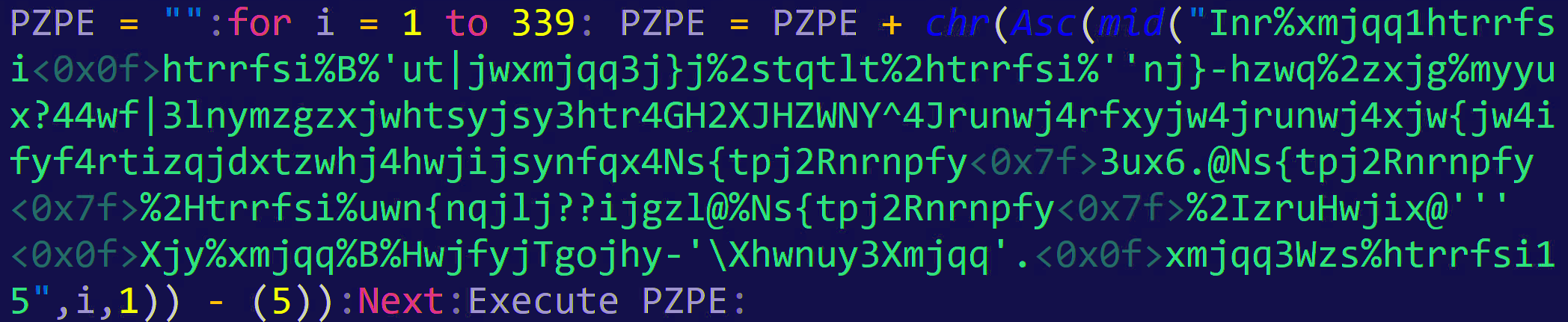
lgwi = "":for i = 1 to 163: lgwi = lgwi + chr(Asc(mid("Inr%xmjqq1htrrfsi�htrrfsi%B%'ut|jwxmjqq3j}j%2stqtlt%2htrrfsi%''Sj|2Nyjr%H?ayj}ya{gxyjxy3y}y%2Ktwhj'''�Xjy%xmjqq%B%HwjfyjTgojhy-'\Xhwnuy3Xmjqq'.�xmjqq3Wzs%htrrfsi15",i,1)) - (5)):Next:Execute lgwi:
Link to GitHub project:
https://github.com/bobby-tablez/VBScrambler
Leave a Reply