Tag: powershell
-
Playing With Process Handles
Process handle overview Let’s talk Handles! A process handle is simply an identifier handled by the system which allows Windows processes to reference and manipulate other processes within the OS environment. It’s essentially a pointer or an access token granted…
-
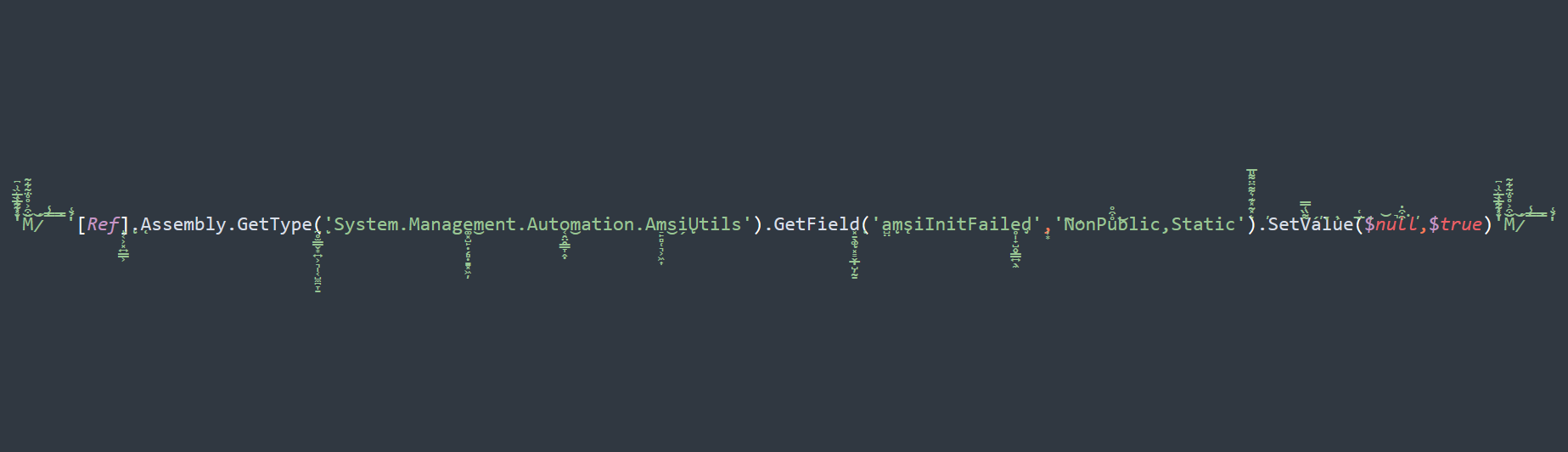
Bypass AMSI Using Combined Unicode Characters
Y̸͎͊ȍ̴̟̺ȗ̸̬r̵̺̔̑ ̶̰͠n̵̺̅͋ȩ̵̢̈́͝ẘ̵̨ ̶̙͓̅̆f̵̮́̚ą̶̼̈́v̴̟̈́̏o̷̢̗̾̆r̴͕̅i̵̩̭͌t̵̞̫͛e̴̙͛́ ̸͍̭͛À̷̧̰̈́M̸̱͙̒̈́S̵͓̓I̵̗̥̿ ̷̝͗ḅ̵͔͋y̵̖̗̋p̴̧̫͆ä̵͓̫́̒s̵̬͊̀s̶̪̉̌.̸̮͂̆͜.̸̬̎͑͜.̷͖̯̕ Okay, this is a strange one. For those of you who are unaware, there are certain Unicode characters that exist that when combined with another similar class of character, they will combine to form two…
-

Deobfuscating PowerShell Code Using Sublime Text
When we think of malware analysis, especially when it comes to the analysis of malicious scripts, we generally don’t think of our noble text editors of anything but… well, text editors. While there are many ways of deobfuscating PowerShell and…
-

Windows Sandbox – Flare VM
This config file will automatically convert a temporary Windows Sandbox environment into a Flare VM for malware analysis. Useful for standing up a “quick” flare-vm test environment on the fly. Additionally, enhanced logging telemetry is also enabled on the host.…
-
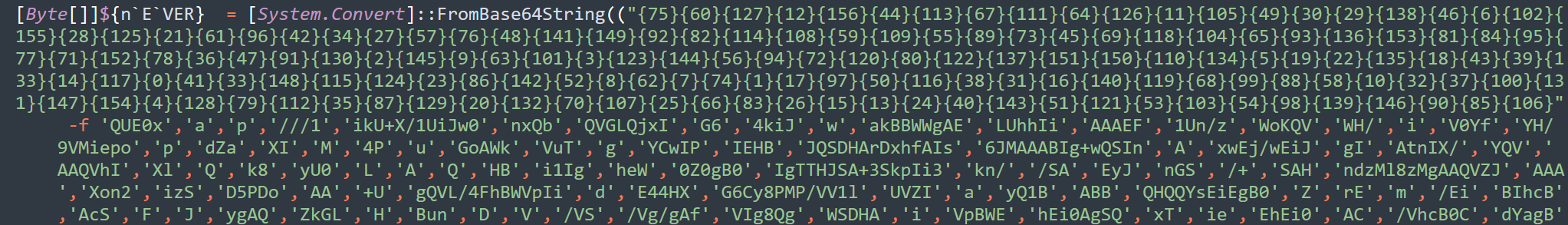
Reordered Format String Deobfuscator
This script simply deobfuscates obfuscated PowerShell files or commands which leverage “Format String Reordering” in order to hide its original code. For more information on this obfuscation technique, see: https://www.securonix.com/blog/hiding-the-powershell-execution-flow/ The script has the ability to deobfuscate format strings in an…
-

Enable All The Logs!
This script automates enhancing logging telemetry on Windows hosts. It is designed specifically with threat detection in mind where logging is critical for detections in SIEM environments or in a lab setting for emulation, validation or for malware analysis. This…