When we think of malware analysis, especially when it comes to the analysis of malicious scripts, we generally don’t think of our noble text editors of anything but… well, text editors. While there are many ways of deobfuscating PowerShell and other scripting language, Sublime gives us a nice all-in-one platform to be able to peel back each layer and understand the obfuscation techniques a bit better.
Threat actors regularly obfuscate their code for two primary reasons: first, to evade AV or EDR detection. The code will look like garbage, but it will (hopefully) execute in the end. The second reason is for counter-analysis purposes. This in the end is an effort to slow down or even stop the analyst or researcher from identifying the original intent of the script.
Fortunately, Sublime Text features some pretty useful packages that we can install and configure to help us analyze these malicious scripts. So let’s take a look at how to setup our environment, and walk through an example using a heavily obfuscated script using Invoke-Obfuscation by Daniel Bohannon.

While this tool is quite dated by current cybersecurity standards, it is regularly used by malware authors to evade AV and AMSI detections currently.
Environment setup
Sublime text runs on pretty much any modern Windows, Linux or macOS system, so grab a copy from their website, install it and you’re half way there.
Next, open up the package manager by hitting Ctrl+Shift+P on Windows, or Command+Shift+P on mac.
When the popup window is displayed, type “install” and you should see an option for: Package Control: Install Package
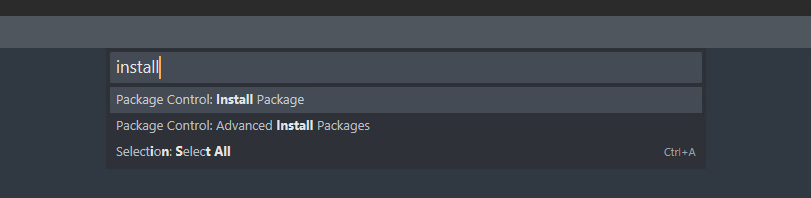
Clicking on the install package option should present a popup stating that package control was successfully installed.
Next, open up the package manager once again, and type “install”, and click the option: “Package Control: Install Package”.
This will open up a new central popup menu with a new search bar. Now, search for “powershell” to install the support package which will allow for useful features such as PowerShell syntax highlighting.
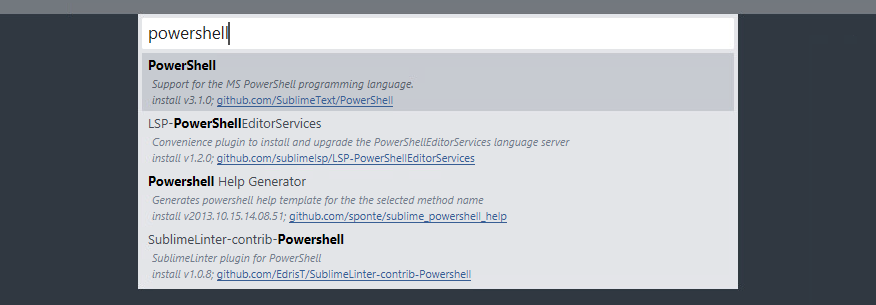
Once clicked, it will appear to have done nothing, but the install job will have kicked off and completed in the background.
Now, you should be able to build or run any PowerShell or .ps1 script from within Sublime Text itself! This is done by first opening or saving a .ps1 file, and selecting the option “Tools –> Build” As you can see in the example below, the actions in the small test script were executed directly from Sublime Text!
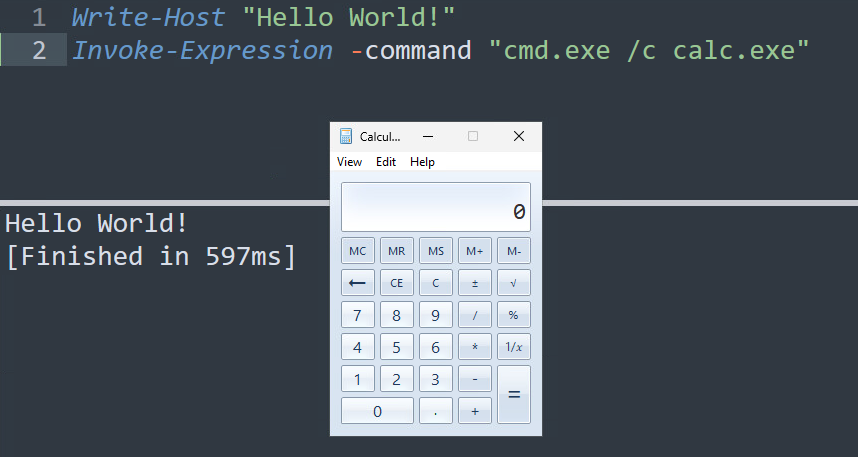
Deobfuscation….
Now that we’re all setup and ready to dive in, let’s open up our saved PowerShell file in Sublime. The file we’ll be using today is a simple PowerShell command which was ran through a couple layers in Invoke-Obfuscation namely string reordering and then special character encoding. The result is the globular mess we see in the header image.
Technically, this process would work in any PowerShell editor such as ISE, however Sublime simplifies the task by providing awesome syntax highlighting, error checking and a clean working environment.
The first step is to identify the code invocation. Invoke-Obfuscation relies heavily on PowerShell invoke expressions to run and execute the code hidden behind the obfuscation.
Typically script blocks are invoked using one of two methods, invoking the content within a parenthesis block “()” or piping the contents into the invoke expression command. For example:
iex(code to invoke)
code to invoke|iex
It’s worth noting that while “iex” is the alias for Invoke-Expression, the code will also be obfuscated. The first step is to look for the invocation pattern, ie: a small block of obfuscated code at the end of the (also) obfuscated string separated by a “|” character, or at the beginning of the script block, code outside of a large “()” block.
In the example of the header, we can identify the invoke expression at hidden in the middle of the script block. Typically, it is at the beginning or end depending on the type of ofbuscation used. It can also be in the middle of the block after a line break “;” character and invoked using “.” or “&” sourcing operators.
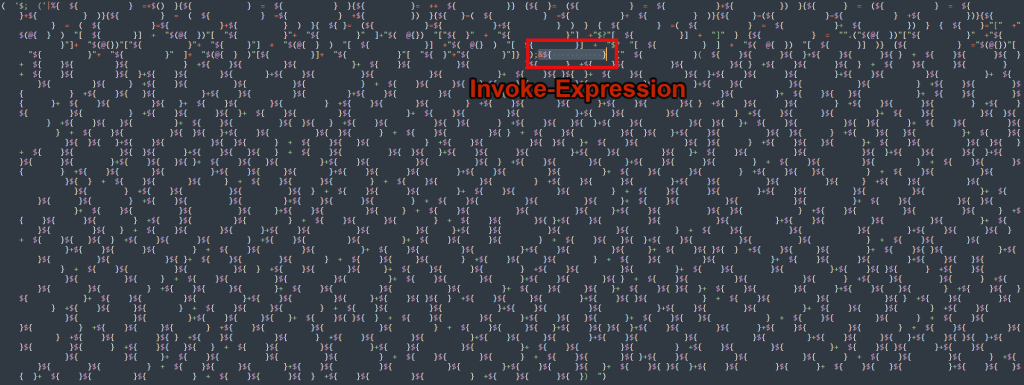
This type of obfuscation is by far the most difficult to analyze as it contains variable names of random lengths which are either special characters or spaces of varying lengths contained within squiggle brackets such as ${ }, which is the case for our invoke expression.
The next step is to simply remove it! Without any kind of invocation, the code will simply print itself. With the invoke deleted out of the code, we get the following output:
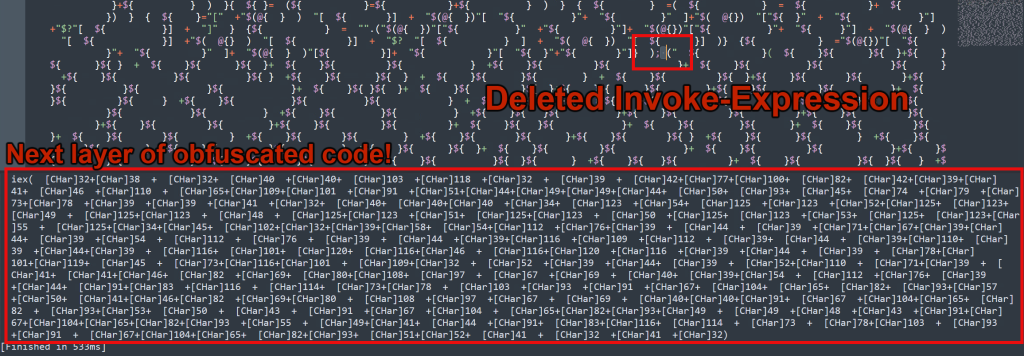
Now, it’s simply rinse and repeat, this time the invoke expression is a bit more obvious, as it is simply an “iex” preceding a block of character array values. Let’s now copy the output, save it as a new file, remove the iex at the start and run it:
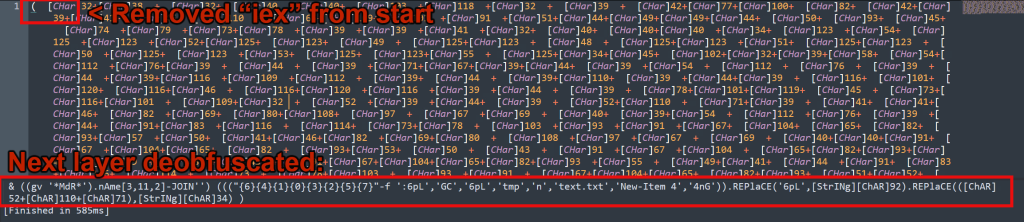
Now we’re getting somewhere! On to layer 3 using the same technique we’ve been using. This time the Invoke-Expression is located at the beginning of the script block using a form of obfuscation which uses a shortened Get-Value (alias: gv) parsing MdR from between wild card characters. The return is “MaximumDriveCount”. That string is then taken and referenced using its index values of 3,11 and 2 and then joined together. The result is… you guess it: iex. There are almost an unlimited methods out there that threat actors use to obfuscate invoke expressions. Many are highlighted in this guide and many more like it out on the internet.
Let’s remove the entire obfuscated invoke from the next layer (& ((gv ‘MdR‘).nAme[3,11,2]-JOIN”)) and give it a run:
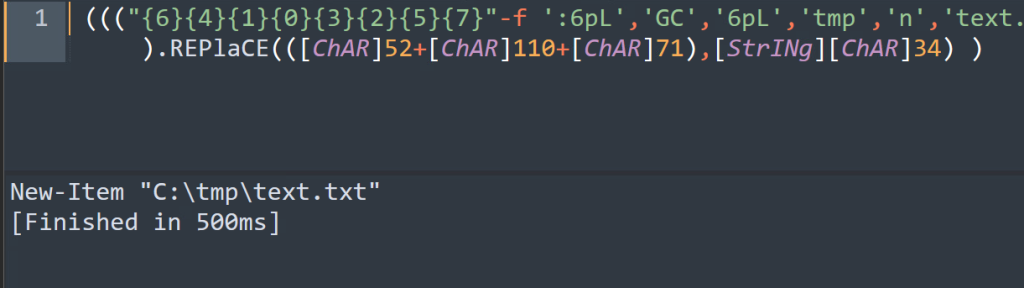
And there we have it! The resulting code in this example simply creates a new text file using the following command:
New-Item "C:\tmp\text.txt"
There are other methods of deobfuscating PowerShell, some probably much more efficient. However, leveraging Sublime Text and peeling back the layers manually one at a time is a worthwhile exercise to get familiar with. Understanding how PowerShell handles code invocation and how to hunt through some of the gnarliest types of obfuscation for the invokes, will make you all the more proficient.

Leave a Reply