Tag: malware-analysis
-

Windows Sandbox – Flare VM
This config file will automatically convert a temporary Windows Sandbox environment into a Flare VM for malware analysis. Useful for standing up a “quick” flare-vm test environment on the fly. Additionally, enhanced logging telemetry is also enabled on the host.…
-
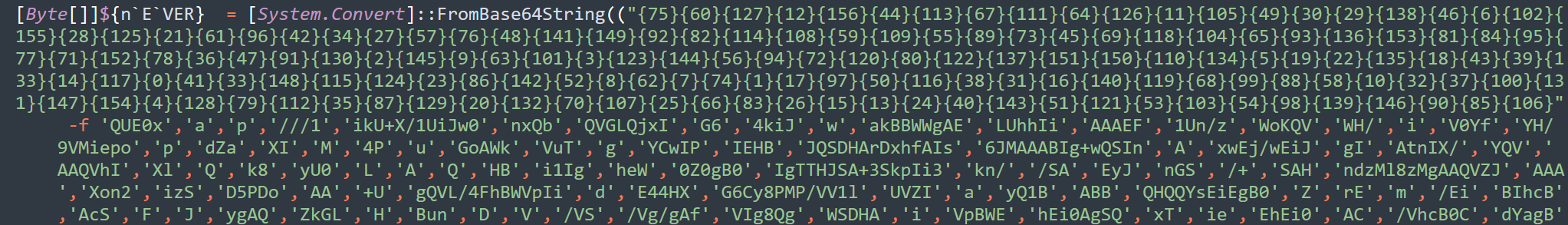
Reordered Format String Deobfuscator
This script simply deobfuscates obfuscated PowerShell files or commands which leverage “Format String Reordering” in order to hide its original code. For more information on this obfuscation technique, see: https://www.securonix.com/blog/hiding-the-powershell-execution-flow/ The script has the ability to deobfuscate format strings in an…
-

Enable All The Logs!
This script automates enhancing logging telemetry on Windows hosts. It is designed specifically with threat detection in mind where logging is critical for detections in SIEM environments or in a lab setting for emulation, validation or for malware analysis. This…
-
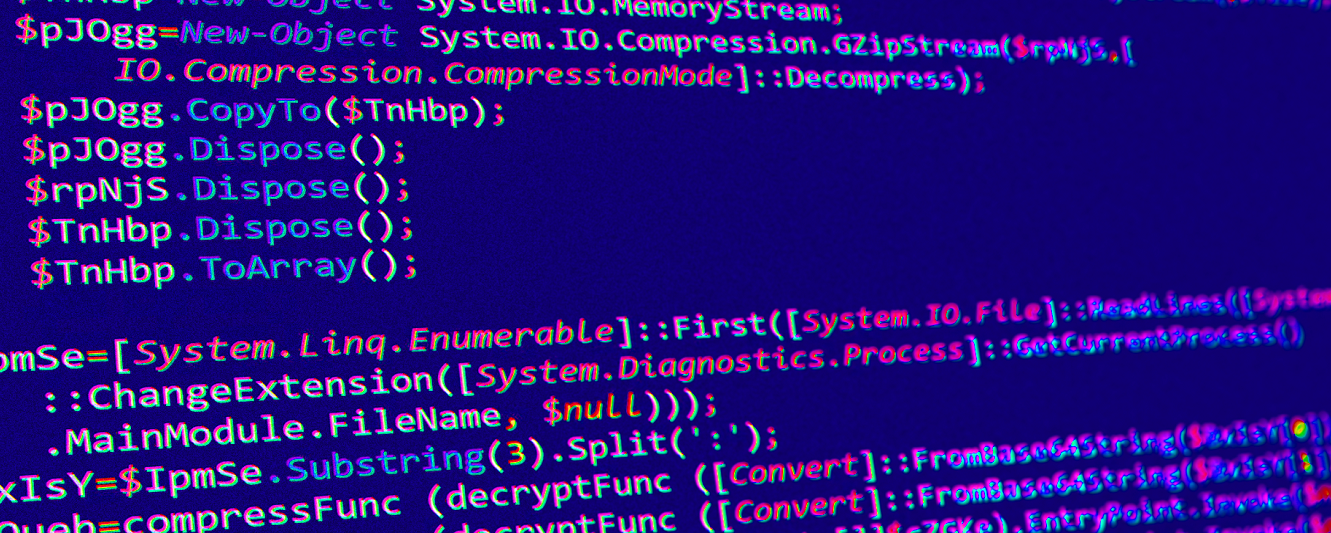
Analysis of Malicious PDF attachments delivering XWorm Payloads
Let’s dive into an interesting attack campaign which attempts to lure unsuspecting victims into downloading and running an Adobe “plugin” in order to deliver a RAT (remote access trojan) known as XWorm. Despite its name, XWorm functions as a RAT…